Frameworks#
In-toto#
In-toto: A framework to secure the integrity of software supply chains.
What is in-toto?
in-toto is designed to ensure the integrity of a software product from initiation to end-user installation. It does so by making it transparent to the user what steps were performed, by whom and in what order. As a result, with some guidance from the group creating the software, in-toto allows the user to verify if a step in the supply chain was intended to be performed, and if the step was performed by the right actor.
Check: https://in-toto.io/
Check here for the github repository.
NIST Security framework#
Whenever you feel the need to draw a process regarding security or risk processes: resist the temptation! The US based NIST organization is a well-known governmental organization that offers great publications on all thinkable subjects regarding security.
One of the simplest, yet most frequently model is displayed here below.
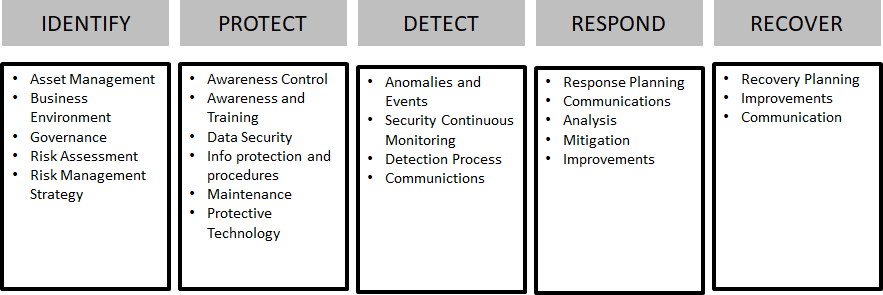
On the NIST site (see references) you can find in-depth information regarding all sub functions of this security framework. The experience is, is that it is far better to check what in your use case needs special attention. If you ever feel the need to create your own security framework, think again. In essence all come down to the high level framework described by the NIST organization. Using a broad used security framework has a number of advantages:
Easier communication with stakeholders;
Easier knowledge and experience transfer between security experts of different organization;
Saves time, time you can use to solve the real context specific issues regarding practice use and implementation of the security functions.
NIST Risk Management Framework RMF#
The NIST Risk Management Framework (RMF) provides a comprehensive, flexible, repeatable, and measurable 7-step process that any organization can use to manage information security and privacy risk for organizations and systems and links to a suite of NIST standards and guidelines to support implementation of risk management programs to meet the requirements of the Federal Information Security Modernization Act (FISMA).
Risk management overview:
https://csrc.nist.gov/projects/risk-management
Search for RMF controls (checklist):
https://csrc.nist.gov/Projects/risk-management/sp800-53-controls/release-search#!/search?version=5.1
Good overview on of all controls:
Open Software Supply Chain Attack Reference (OSC&R)#
A great framework for Releasing Secure Products.
Open Software Supply Chain Attack Reference (OSC&R)
Make security a part of product development.
Check: https://pbom.dev/
The Update Framework#
The Update Framework (TUF) helps developers maintain the security of software update systems, providing protection even against attackers that compromise the repository or signing keys. TUF provides a flexible framework and specification that developers can adopt into any software update system.
TUF is hosted by the Linux Foundation as part of the Cloud Native Computing Foundation (CNCF) and is used in production by various tech companies and open source organizations.
Check: https://theupdateframework.io/
This project is a Linux Foundation project under the Cloud Native Computing Foundation.
Supply-chain Levels for Software Artifacts (SLSA)#
Supply-chain Levels for Software Artifacts, or SLSA (“salsa”). It’s a security framework, a checklist of standards and controls to prevent tampering, improve integrity, and secure packages and infrastructure. It’s how you get from “safe enough” to being as resilient as possible, at any link in the chain.
Hint
More information: Check the SLSA security framework
Secure Software Development Framework (SSDF)#
Few software development life cycle (SDLC) models explicitly address software security in detail, so secure software development practices usually need to be added to each SDLC model to ensure that the software being developed is well-secured. This document recommends the Secure Software Development Framework (SSDF) – a core set of high-level secure software development practices that can be integrated into each SDLC implementation.
Check NIST SP 800-218 Secure Software Development Framework (SSDF)
Open Cybersecurity Schema Framework (OCSF)#
The Open Cybersecurity Schema Framework is an open-source project, delivering an extensible framework for developing schemas, along with a vendor-agnostic core security schema. The framework is made up of a set of data types, an attribute dictionary, and the taxonomy. It is not restricted to the cybersecurity domain nor to events, however the initial focus of the framework has been a schema for cybersecurity events. Check and use: Cybersecurity Schema Framework
Note
OCSF is licensed under the Apache License 2.0. The repository home is: ocsf/
VERIS Framework#
The Vocabulary for Event Recording and Incident Sharing (VERIS) is a set of metrics designed to provide a common language for describing security incidents in a structured and repeatable manner. VERIS is a response to one of the most critical and persistent challenges in the security industry - a lack of quality information. VERIS targets this problem by helping organizations to collect useful incident-related information and to share that information - anonymously and responsibly - with others.
Check: https://verisframework.org/
Repository: vz-risk/veris
Frameworks#
NIST Cybersecurity Framework
For industry, government, and organizations to reduce cybersecurity risks
Open Security Architecture (OSA)
OSA distills the know-how of the security architecture community and provides readily usable patterns for your application. OSA shall be a free framework that is developed and owned by the community.
Software Assurance Maturity Model
The Software Assurance Maturity Model (SAMM) is an open framework to help organizations formulate and implement a strategy for software security that is tailored to the specific risks facing the organization.
