The goal of an architecture review is to identify and highlight all security weaknesses in a system. Our security review is always profitable. For a new or already developed system. Included in the review are relevant designs, business processes, applications, (cloud) environment , interfaces (internal and external) and infrastructure dependencies. You can use the result of our review to improve your cyber security resilience.
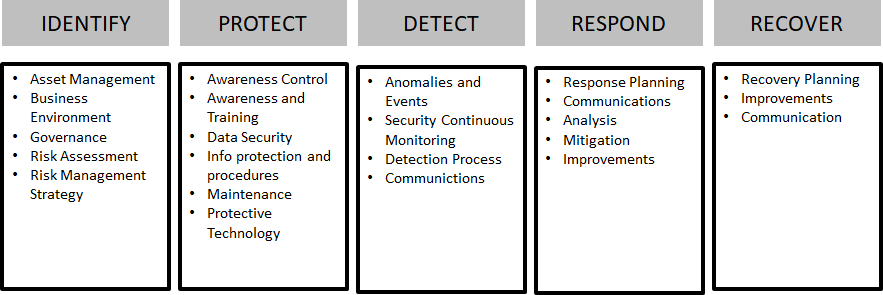
We will perform a comprehensive inspection of how each application is designed, including application structure, data storage, interfaces , infrastructure design, and more. We will work with your development team to determine the security posture of your current architecture. And to search for security simplification improvements. A full review of application or cloud structure, authentication, configuration, and services will be performed to give you advice on your current risks.
At the end of the Secure Architecture Review, we deliver a full report with the relevant discoveries, findings, and recommendations for improvement of your security landscape. This report gives you opportunities to:
- Simplify your security landscape. So make it better.
- Improve your security process using an agile approach that meets your current development agenda.
- Further minimize security and privacy risks in a more cost effective way.
We make use of the Open Reference Architecture for Security and Privacy for your security architecture review.
We will examine processes and technical configurations such as:
- SDLC Style
- Coding Practices
- Testing Procedures
- Code Promotion Process (CICD)
- Authentication
- Authorization
- Encryption
- Web Servers
- Application Servers
- Database
- Servers
- Firewalls (Web, Network)
Due to covid-19 we work remote whenever possible. We use only high secure and private online collaboration tools.